DO-326A / ED-202A Intro to Aviation Cyber-Security White Paper
Are cyber threats the nemesis of aviation… or is it DO-326/ED-202?
In 2015, a passenger who also happened to be a cybersecurity researcher walked onto a commercial-flight airplane with a laptop and successfully hacked its network. According to a Federal investigation, this passenger accessed the thrust system of the plane and made it fly higher than the pilot intended. As terrifying as it might be to hear that someone could hack a commercial flight and take control, this story fortunately ended without an accident, though it highlighted some very concerning vulnerabilities on commercial flights. Clearly, there were security holes that needed filling. Four years later, DO-326A and ED-202A became the only Acceptable Means of Compliance (AMC) for cybersecurity airworthiness certifications in the U.S. and Europe, and many of those vulnerabilities were eliminated. In reality, RTCA and EUROCAE had already been frantically developing a certification standard for almost a decade. The FAA and EASA made the earliest versions of DO-326/ED-202 as mandatory as practical at any given time, and by 2018, it was already widely regarded as an “Acceptable Means of Compliance” (AMC): a de-facto mandatory standard. How did the standard go from being AN ACM to being THE ACM for cybersecurity in aviation? Good question. The answer is that the need was simply too obvious to ignore. “Digital aircraft” are already as commonplace as the aircraft itself, as natural as aircraft wings or engines, to the extent that modern aircraft could be regarded as winged and powered computers. The turn of the millennium saw the rise of the next aviation digital phenomenon: the connected aircraft, in which everything is plugged into the internet and to everything else. While digital radio-systems, GPS, ACARS, ADS-B and more have been integral components of passenger aircraft for decades, today’s new aircraft contain thousands of processors performing both independent and intricately related operations. Whereas old aircraft had hundreds of processors in a “closed” system, today’s aircraft architectures are connected to the internet, necessitating more caution. Hence, the development of DO-326 and ED-202.
Contents:
- What is DO-326/ED-202?
- Is DO-326/ED-202 Necessary?
- Is DO-326/ED-202 Compliance Mandatory?
- DO-326A/ED-202 Guidance and Recommendations
There are some major questions that need to be dealt with prior to engaging in any DO-326/ED-202 project:
✓ What is Cyber-Threat / Cyber-Security?
✓ How does it relate to Aviation/Aircraft?
✓ What guidance/standards for Cyber-Security exist today?
✓ To what extent are the existing standards applicable to Aviation/Aircraft?
✓ What is “DO-326/ED-202”, and why couldn’t just “ARP-4754/DO-178” be applied?
✓ What is the “DO-326/ED-202-set”?
✓ To what extent is the “DO-326/ED-202-set” mandatory?
✓ What are the “326/202-set” “guidance/recommendations” (and what they are not…)? ✓ What does it take to meet the “326/202-set” “guidance/recommendations”?
✓ How can the “326/202-set” “guidance/recommendations” be efficiently met?
Answers to these questions are found below and in greater detail within our downloadable DO-326 Whitepaper.
What is DO-326/ED-202?
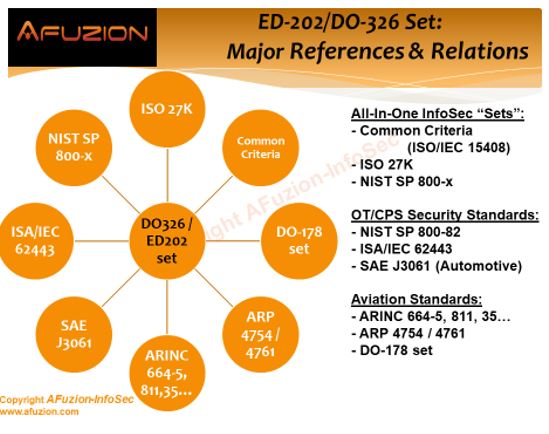
When the European and American aviation industry embarked on their standard-setting process circa 2005, no existing cybersecurity standard at the time could provide a ready-made solution. So, in 2006, EUROCAE formed Working Group 72 (WG-72), and in 2007 RTCA formed Special Committee 216 (SC-216). Both groups named the initiative “Aeronautical Systems Security,” and the process that yielded DO-326/ED-202 and their companion ecosystem documents began. The first resulting documents, ED-202 in Europe and DO-326 in the U.S., were both named “Airworthiness Security Process Specification.” The original DO326/ED-202 documents were intended to serve as guidance for the information security of the development phase of aircraft from inception to certification and deployment. The original document language clearly stated that DO-326 and ED-202 are the first of a series of documents on Aeronautical Systems Security that together will address information security for the overall Aeronautical Information System Security (AISS) of airborne systems with related ground systems and environment. But there were many more changes to come. In 2018, the DO-326/ED-202 set came to include four different standards: DO-326A, ED-202A, DO-356A, and ED-203A. DO-326/ED-202 were heavily based on the already published ISO/IEC 27005 of the ISO27K family, and on the de facto industry standard, SAE ARP 4754, “Certification Considerations for Highly-Integrated or Complex Aircraft Systems.” DO-356A and ED-203A, known as Information Security Guidance for Continuing Airworthiness, were effectively supplementary, providing a practical guide for avionics developers and engineers to actually apply DO-326 and ED-202. In all, the new standards created a useful continuum with earlier certifications in a relatively seamless manner.
Table of Contents
Is DO-326/ED202 Necessary?
However, anyone who ever had even a brief acquaintance with ARP4754 or RTCA’s DO-178, “Software Considerations in Airborne Systems and Equipment Certification,” should be wondering, why were additional standards necessary? Why couldn’t information security simply be part of ARP4754 and/or DO-178, especially in light of both going through major revisions at the time?
The simple, practical reason is stated in a DO-326/ED-202 companion document, published a few years after the original standards: “Airworthiness security is its own discipline, needing unique expertise, and requires its own analysis techniques and assurance considerations.” In other words, information security in the air has its own category, separate from general avionics safety and from other security considerations.
In addition, information security in aviation is not necessarily all about software, as it involves quite a few other aspects of aviation. For example, DO-236A and ED-202A also cover security for hardware, including physical processors and memory. So the standards don’t fit with compliance certifications that only apply to software. Therefore, ARP 4754 and DO-178 were simply focused on other things outside of cybersecurity issues.
The final deterrent from integrating information security into ARP 4754 and/or DO-178 was the fact that their source of legitimacy, FAA/EASA AC/AMC 25.1309 “System Design and Analysis”, wrote the definition for events covered by the documents in such a way that it automatically excluded deliberate human interference. “Event: An occurrence which has its origin distinct from the airplane, such as atmospheric conditions (e.g. gusts, temperature variations, icing and lightning strikes), runway conditions, conditions of communication, navigation, and surveillance services, bird-strike, cabin and baggage fires…” And so on. The term is not intended to cover sabotage, so it can’t cover the concern of hackers or tampering.
Not to mention, regulators knew that any change to FAA/EASA formal documents could delay the approval process for a decade or so. Reacting to the need to close the information security regulatory gap immediately, both WG-72 and SC-216 were encouraged to develop separate documents that would tightly coordinate with ARP 4754 and DO-178, so they did.
The first steps following the publication of DO-326 & ED-202 were:
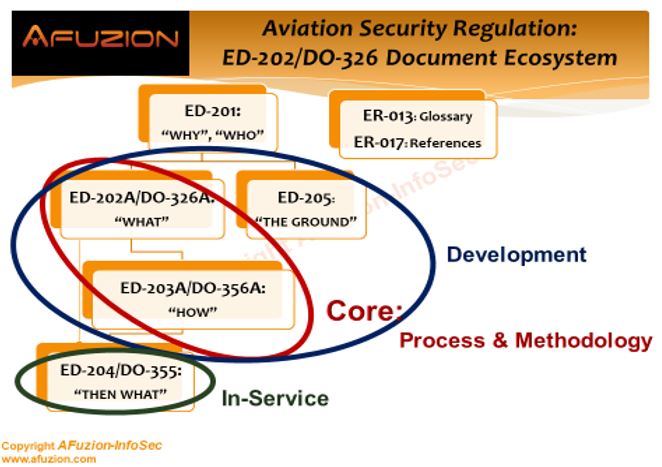
- “Clean” DO-326/ED-202 to make it a core document that would only cover the WHAT of the certification process as opposed to the HOW. The revised version, DO-326A/ED-202A, was published in 2014.
- Publish a new document, DO-355/ED-204, “Information Security Guidance for Continuing Airworthiness,” to cover the post-production, in-service phase: also in 2014. The new DO-355/ED-204 incorporated sections directly influenced by DO-326/ED-202.
- Publish a new companion document that addresses the HOW of the certification process. The new pair was called DO-356/ED-203, “Airworthiness Security Methods and Considerations.”
However, at this third stage, the different nature of EUROCAE’s WG-72 group and RTCA’s SC-216 committee started to take its toll, as the resulting DO-356 (published in 2014) and ED-203 (published in 2015) took different approaches, and were not technically identical like the other members of the series. Additionally, WG-72, applying its holistic approach, published in 2015 a document of its own, without an SC-216 equivalent: ED-201, “Aeronautical Information System Security (AISS) Framework Guidance,” intended as a strategic, top-level document to provide a “big picture,” aided by two background reports: ER-013, “Aeronautical Information System Security Glossary” in 2015, and ER-17, “International Aeronautical Information Security Activity Mapping Summary” in 2018.
At this stage, an FAA rulemaking committee, coordinating with EASA, ANAC (Brazil), and TCCA (Canada) intervened, and among a variety of other issues approached, brought the EUROCAE and RTCA committees together again. This resulted in revisions to both DO-356 and ED-203, which were published in 2018 as DO-356A/ED-203A, unifying their technical content. However, ED-201 was not matched by a DO equivalent, as it was not deemed a “working document” but rather an “orientation document,” meaning it provides a topic overview instead of being a detailed guide.
Meanwhile, WG-72 went on to produce another document of its own, ED-205, “Process Standard for Security Certification/Declaration of Air Traffic Management/Air Navigation Services (ATM/ANS) Ground Systems,” again without an SC-216 equivalent. This time, an equivalent was unnecessary, since the FAA manages most of its air-traffic ground-components internally, while the EASA is a coalition of a few dozen civilian aviation authorities that have their own individualized air traffic processes.
Thus, as of early 2019, the DO-326/ED-202 set comprises:
- The core guidance and considerations: DO-326A/ED-202A and DO-356A/ED-203A
- The in-service guidance: DO-355/ED-204, based on the core guidance
- The top-level documents: ED-201, ER-013, ER-017, serving as philosophy guidelines
- The ground systems standard: ED-205, intended for mainly European usage, originally scheduled to be published in 2019
Is DO-326/ED-202 Compliance Mandatory?
Like most other RTCA and EUROCAE documents, the DO-326/ED-202 set is considered a de facto aviation industry standard, as official mandates keep coming in. While “guidelines” is in title, the lack of any meaningful alternatives means these guidelines are treated as standards which need to be considered. As such, avionics engineers and manufacturers must demonstrate their intent to follow the guidelines laid out in the set.
So, the very clear recommendation on this was for the FAA to “consider RTCA standards DO-326, DO-356 and DO-355 and EUROCAE standards ED-201, ED-202, ED-203, ED-204 as acceptable guidance materials to comply with the security rule 25.13xx for large transport aircraft for new Type type-certifications or new significant major changes or when the applicant elects to use them on a voluntary basis,” which in regulatory parlance translated to “FAA: make it mandatory now.”
This recommendation was well harmonized with EASA’s task force RMT.0648, developing the “Certification Specifications for product design” and task force RMT.0720, developing the “Rules for risk management within organizations and service providers.” Both of these were horizontal guidance, designating the DO-326/ED-202 set, published in 2020.
In Europe, on July 1st, 2020, EASA made public its “ED Decision 2020/006/R”, adopting, with minor revisions, EASA’s February 2019 Notice of Proposed Amendment (NPA) 2019-01, “Aircraft cybersecurity, effective since 01/01/2021. Details about this new guidance are included in the whitepaper for download.
In all, as EASA (Europe), ANAC (Brazil), and TCCA (Canada) actively cooperated with the FAA ARAC ASISP WG, the clear meaning of this seemed to be that the DO-326/ED-202 set is becoming mandatory, and very soon, all over the world. However, the standard technically continues to be a recommendation rather than a mandate even now.
As a final note, some aspects of the DO-326/ED-202 set that were already made mandatory by the FAA:
✓ FAA Policy Statement PS-AIR-21.16-02 Rev. 2, “Establishment of Special Conditions for Aircraft Systems Information Security Protection” states that the FAA “…will issue special conditions for initial type certificate (TC), supplemental type certificate (STC), amended TC, or amended STC applications for aircraft systems connecting to non-trusted services (e.g., non-governmental) and networks…” As the said revision 2 is the product of the ARAC ASISP WG, and as the DO-326/ED-202 set was recommended as AMC, the meaning of this policy is that de-facto, the DO-326/ED-202 set is now the norm for this type of certification.
✓ FAA Advisory Circular AC 119-1, “Airworthiness & Operational Authorization of Aircraft Network Security Program (ANSP)” uses the “in-service” part of the set: DO- 355, which relies on DO-326 & DO-356.
✓ FAA Advisory Circular AC 20-140C, “Guidelines for Design Approval of Aircraft Data Link Communication Systems Supporting Air Traffic Services (ATS)” uses the “core” and the “in-service” full set: DO-326, DO-356 & DO-355.
✓ Advisory Circular (AC) 120-76D: “Authorization for Use of Electronic Flight Bags” uses (AC) 20-140C, which relies on the entire DO-326 set.
✓ TSO-C159d (2018): “Next Generation Satellite Systems (NGSS) Equipment” which uses the DO-326 set (DO-355).
DO-326A/ED-202 Guidance and Recommendations
As for the guidance/recommendations that are included in the set, these can be roughly described as:
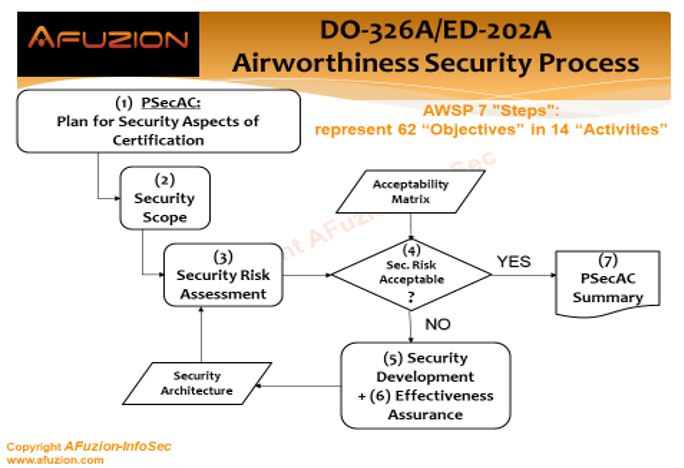
1) The “Airworthiness Security Process” (AWSP), mostly detailed in DO-326A/ED-202A, that outlines the major steps, activities and objectives of security certification for airworthiness:
- AWSP comprises seven steps: Plan for Security Aspects of Certification, Security Scope Definition, Security Risk Assessment, Risk Acceptability Determination, Security Development, Security Effectiveness Assurance, and Communication of Evidences.
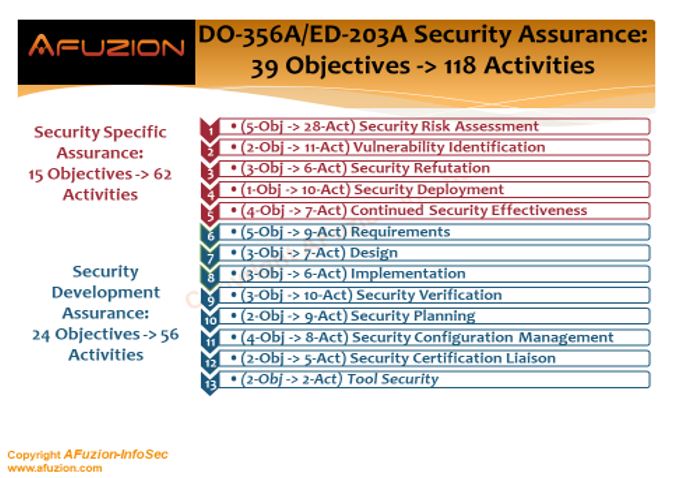
- These seven steps are detailed into 14 activities: Plan for Security Aspects of Certification (PSecAC), Plan for Security Aspects of Certification Summary (PSecAC Summary), Aircraft Security Scope Definition (ASSD), Preliminary Aircraft Security Risk Assessment (PASRA), Aircraft Security Risk Assessment (ASRA), System Security Scope Definition (SSSD), Preliminary System Security Risk Assessment (PSSRA), System Security Risk Assessment (SSRA), Aircraft Security Architecture and Measures (ASAM), Aircraft Security Operator Guidance (ASOG), Aircraft Security Verification (ASV), System Security Architecture and Measures (SSAM), System Security Integrator Guidance (SSIG), and System Security Verification (SSV).
- These 14 activities include 62 objectives (combined) to be met.
- Detailed “Acceptable Means of Compliance” (AMC) – provided mostly in DO-356A/ED-203A.
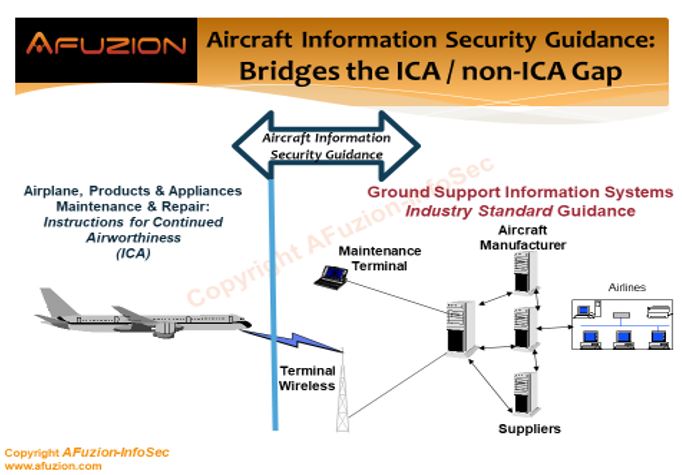
2) “Guidance for Continuing Airworthiness,” mostly provided by DO-355/ED-204, but supported by the core documents of the set as well. This guidance covers the following eleven aspects: Airborne Software handling, Aircraft Components handling, Aircraft Network Access Points, Ground Support Equipment (GSE), Ground Support Information Systems (GSIS), Digital Certificates, Aircraft Information Security Incident Management, Operator Aircraft Information Security Program, Operator Organization Risk Assessment, Operator Personnel Roles & Responsibilities, and Operator Personnel Training. See AFuzion’s DO-326A / ED-202A basic training or our advanced training course for additional details. Combined, the AWSP and Guidance for Continuing Airworthiness form one integrated entity that comprises a complete set of information security AMC for achieving and maintaining airworthiness throughout the entire aircraft life cycle.
See the following graphic, excerpted from AFuzion’s DO-326A / ED-202A Cyber-Security Basic Training, 2 Days (reprinted with permission from AFuzion Infosec)
A crucial aspect of information security is time. It is not merely a one-way safety-type process that has a clear end point and then retreats to just monitoring. Instead, InfoSec is a continual struggle against any potential attacks and attackers. That struggle is constantly evolving, even if nothing else happens concerning the said system. Thus, any modification, addition, removal or even altered function should be re-processed according to the DO-326/ED-202 set in order to assess any issues time may have wrought.
Furthermore, even the mere passage of time, without any modification of the system or its functions can bring changes in the hostility of the cyber-environment, so keeping up with the DO-326/ED-202 set would require periodic risk analysis in order to assess whether the system is still as secure as originally intended. Both the DO-326/ED-202 & DO-356/DO-203 “core” development phase documents and the DO-355/ED-204 “continued airworthiness” phase document need to be followed on this aspect.

Information Request Form
Please provide the following information to receive your full Whitepaper
Other Free Resources
- Free 30-minute tech telecon to answer any of your tech Q’s
- Free Sample Certification Checklist
- Free AFuzion Training Video Sample
- Request invitations to future AFuzion tech webinars, fee waived (free)